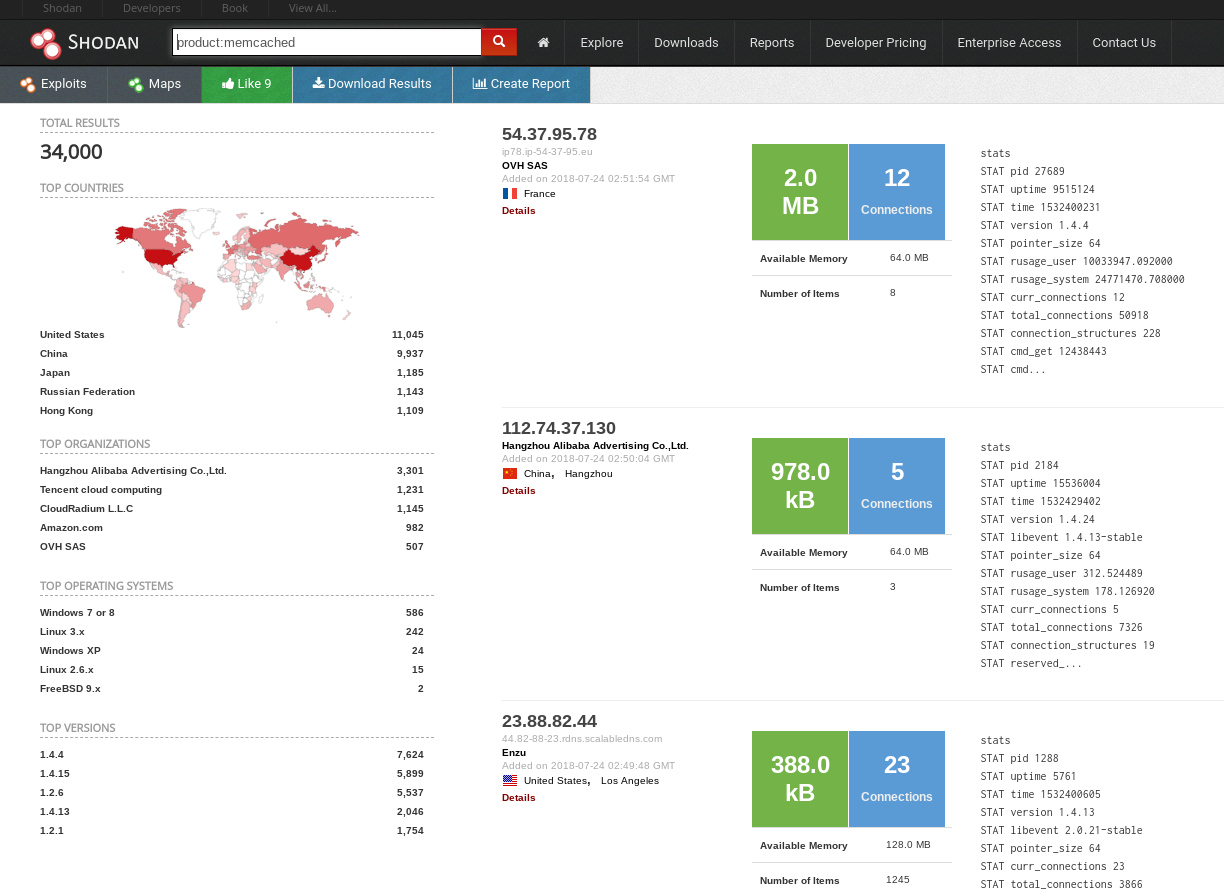
Everyone on the internet knows what a search engine is. It allows you to find internet connected resources (webpages) quickly and easily without having to catalog the web yourself. Well Shodan.io is a search engine used by researchers and hackers to find Internet of Things devices connected to the internet (printers, webcams, industrial systems, WindowsXP, etc).
The purpose of this article is to provide some hyperlinked examples to help the Open Source Intelligence student play with Shodan and make it immediately useful.
This article will provide some examples of how to find webcams connected to the internet.
While you will find thosands that are unprotected (no username or password required) others will be protected but have the default password enabled. Where can you find webcam default passwords? Just search the net but here is one called iSpy to get you started.
Many of these searches will require a free Shodan account so make sure you create one.
I am providing this information for educational purposes only. Don’t do anything illegal.
html:"DVR_H264 ActiveX" - Security Digital Video Recorderstitle:camera - This is a quick search that lists anything with the word camera in it
webcam has_screenshot:true - This search lists any device that self identifies as a webcam and where Shodan has a screenshot.
Server: IP Webcam Server "200 OK" - android IP webcam serverserver: webcampxp - Looking for a very popular windows Webcam server software
title:”blue iris remote view” - Webcams using the Blue Iris webcam management software
product:”Yawcam webcam viewer httpd - Yet Another Webcam is a free webcam publishing server software.
title:”IPCam Client” - Devices using the IPCam software
title:”+tm01+” - loads of unsecured Linksys webcams
Others
I will be posting more articles about other interesting Shodan searches but here are a couple extra to wet your appetite.
"230 login successful" port:"21" - Find FTP servers without logins